| .github | ||
| cmd | ||
| config | ||
| debian | ||
| docker | ||
| mk | ||
| pkg | ||
| rpm | ||
| scripts | ||
| test | ||
| windows | ||
| .dockerignore | ||
| .gitignore | ||
| .gitmodules | ||
| .golangci.yml | ||
| .yamllint | ||
| azure-pipelines.yml | ||
| CONTRIBUTING.md | ||
| Dockerfile | ||
| Dockerfile.debian | ||
| go.mod | ||
| go.sum | ||
| LICENSE | ||
| make_chocolatey.ps1 | ||
| make_installer.ps1 | ||
| Makefile | ||
| README.md | ||
| SECURITY.md | ||
| wizard.sh | ||

CrowdSec is an open-source and participative security solution offering crowdsourced server detection and protection against malicious IPs. Detect and block with our Security Engine, contribute to the network, and enjoy our real-time community blocklist.

Features & Advantages
Versatile Security Engine
CrowdSec Security Engine is an all-in-one IDS/IPS and WAF.
It detects bad behaviors by analyzing log sources and HTTP requests, and allows active remedation thanks to the Remediation Components.
Detection rules are available on our hub under MIT license.
CrowdSec Community Blocklist
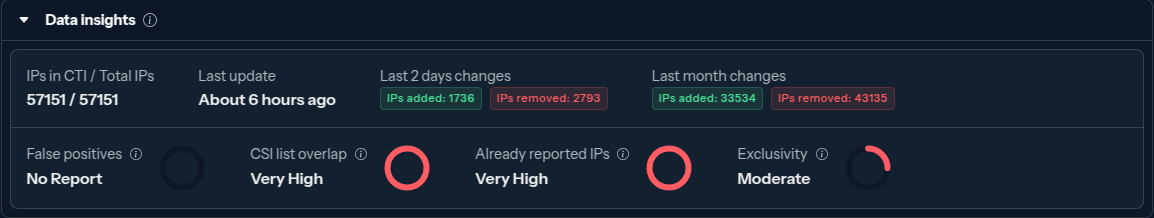
The "Community Blocklist" is a curated list of IP addresses identified as malicious by CrowdSec. The Security Engine proactively block the IP addresses of this blocklist, preventing malevolent IPs from reaching your systems.
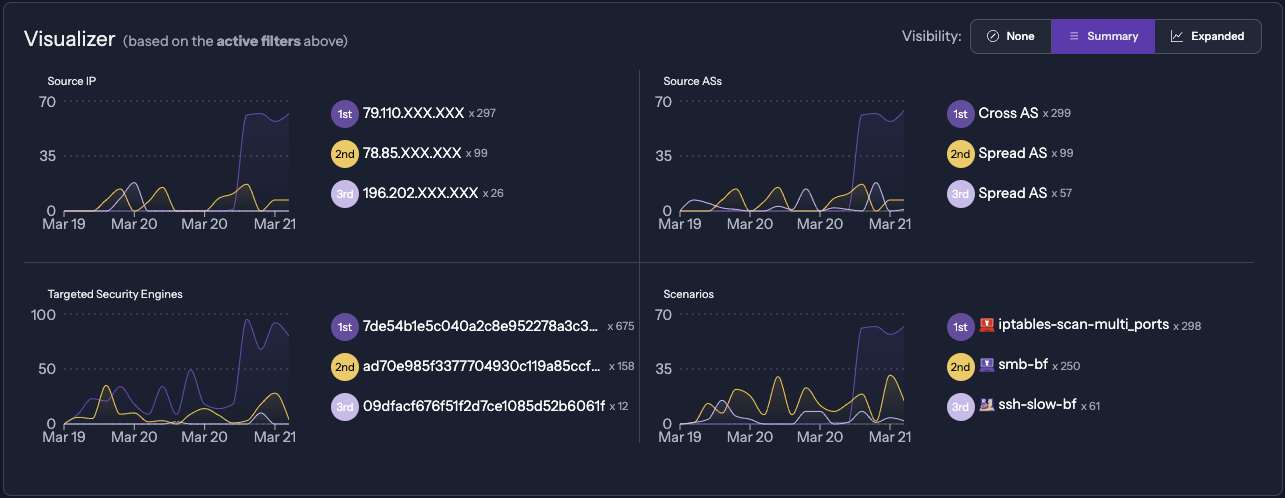
Console - Monitoring & Automation of your security stack
Multiple Platforms support
Outnumbering hackers all together
By sharing the threat they faced, all users are protecting each-others (hence the name Crowd-Security). Crowdsec is designed for modern infrastructures, with its "Detect Here, Remedy There" approach, letting you analyze logs coming from several sources in one place and block threats at various levels (applicative, system, infrastructural) of your stack.
CrowdSec ships by default with scenarios (brute force, port scan, web scan, etc.) adapted for most contexts, but you can easily extend it by picking more of them from the HUB. It is also easy to adapt an existing one or create one yourself.
Installation
Resources
- Console: Supercharge your CrowdSec setup with visualization, management capabilities, extra blocklists and premium features.
- Documentation: Learn how to exploit your CrowdSec setup to deter more attacks.
- Discord: A question or a suggestion? This is the place.
- Hub: Improve your stack protection, find the relevant remediation components for your infrastructure.
- CrowdSec Academy: Learn and grow with our courses.
- Corporate Website: For everything else.